eco survey reveals: One-third of the surveyed IT decision-makers have not yet taken any measures to fulfil the increased security requirements of NIS2.
- 40 per cent of the surveyed IT managers are not aware of the new legal regulation
- 8 per cent have not yet taken any measures to prepare for the increased IT security requirements resulting from NIS2
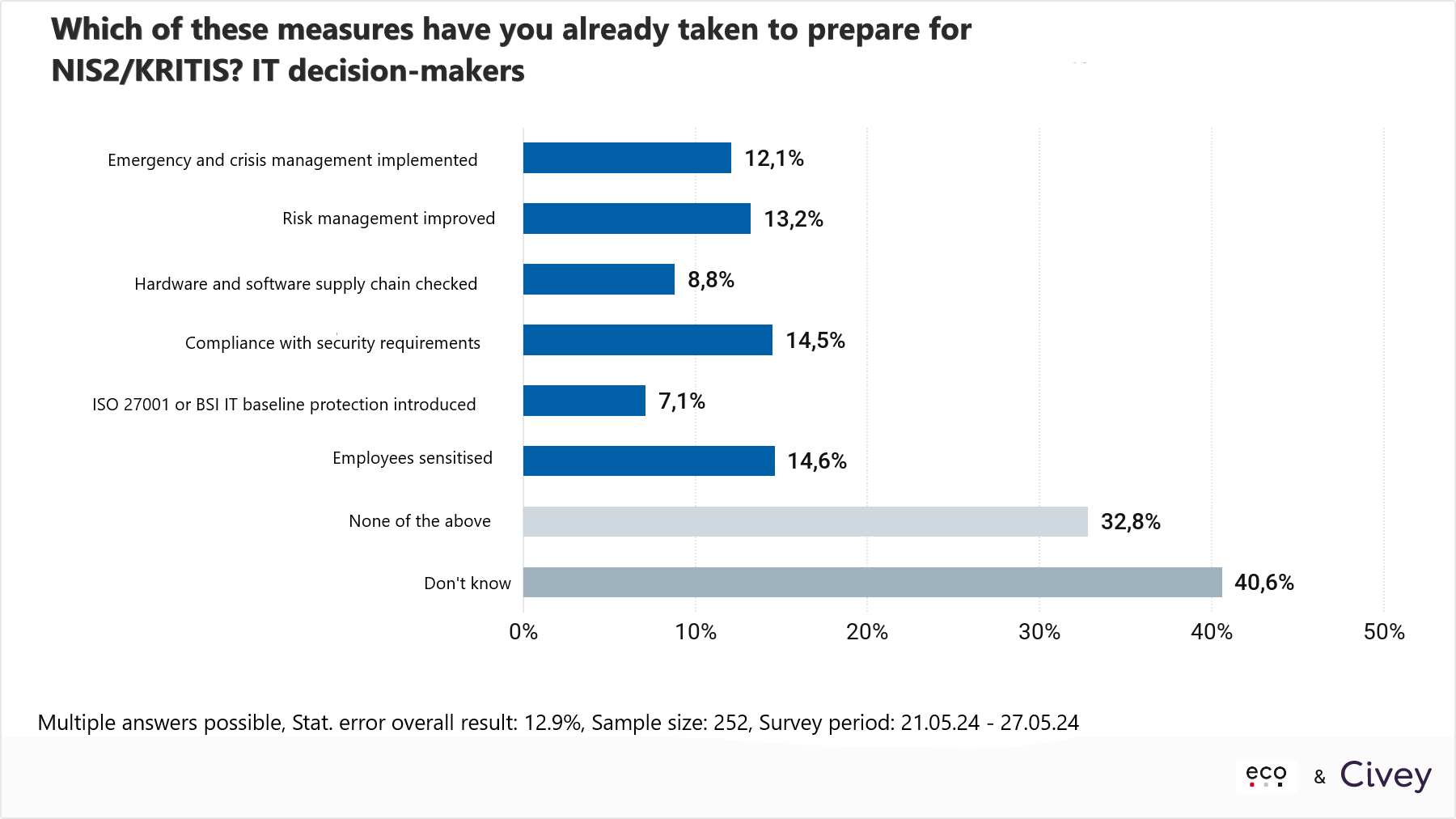
- Only 13.2 per cent of companies have improved their IT risk management
Many companies in Germany have not yet prepared for the future requirements of the NIS2 directive. The European Cybersecurity Directive sets out criteria for identifying operators of critical facilities and other regulated organisations and specifies minimum standards for their information security. According to the current status, it is to be transposed into German law by 17 October 2024. A current draft of the German NIS2 Implementation Act (NIS2UmsuCG) shows that the number of affected companies has increased significantly, from 2,000 to over 30,000.
The directive explicitly requires compliance with ten risk management measures in the area of cybersecurity. However, only 13.2 per cent of companies in Germany have improved their risk management accordingly. This was revealed in a survey of 250 IT decision-makers conducted by the market research institute Civey on behalf of the eco Association. Only 14.6 per cent have already raised employee awareness. 14.5 per cent say they comply with security requirements. 12.1 per cent have implemented an emergency and crisis management system. Only 7.1 per cent have introduced the industry standards ISO 27001 or BSI IT baseline protection. A third of IT decision-makers in Germany state that they have not yet implemented any of the measures mentioned. Of those surveyed, 40.6 per cent said they were unable to provide information and answered “don’t know”.
Tens of thousands of companies in Germany will be subject to EU regulation for the first time ever
The eco Association urgently advises affected IT managers to prepare now for the stricter requirements that are expected to come into force in autumn. Here are five tips:
- If not already done, implement a Business Continuity Management (BCM): Invest now in technical and organisational tools to protect operations from crises and threatening outages – and if something does happen, restore them quickly and in a controlled manner.
- Manage your cybersecurity risks professionally and transparently: Analyse your IT structure – both internally and with service providers – and derive state-of-the-art protective measures. This ranges from attack detection systems to cyber hygiene, which means, for example, ensuring adequate password lengths and securely separated network segments.
- Check your supply chain security: If you are an operator of critical systems, it is your duty to ensure the compliance of your suppliers, including software manufacturers and infrastructure providers. This applies not only to cloud and service providers, but also to the procurement, development and maintenance of your IT systems.
- Install comprehensive IT baseline protection: In addition to technical aspects, infrastructural, organisational and personnel topics are also considered. This includes procedures for the use of cryptography and all measures that reduce IT security risks posed by human factors. Use multi-factor authentication and secure communication systems, even in an emergency: printed emergency manuals and classic radios are invaluable if your IT fails completely.
- Training, education and awareness-raising: Empower your workforce and management bodies and raise awareness of security risks. Particularly vulnerable target groups should be familiarised with social engineering and a range of other malicious activities that are not always IT-related – for example, an AI-alienated voice on the phone can successfully impersonate the CEO.
Download graphic
Download photo of Ulrich Plate, Head of the eco KRITIS Competence Group