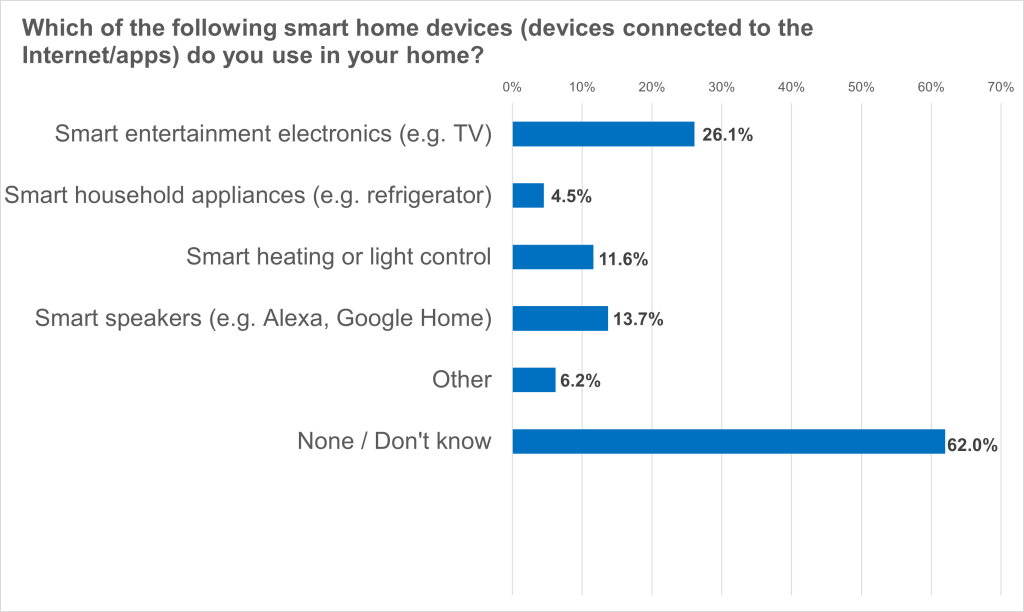
- 38 per cent of Germans use smart home devices, especially smart consumer electronics (26.1 per cent)
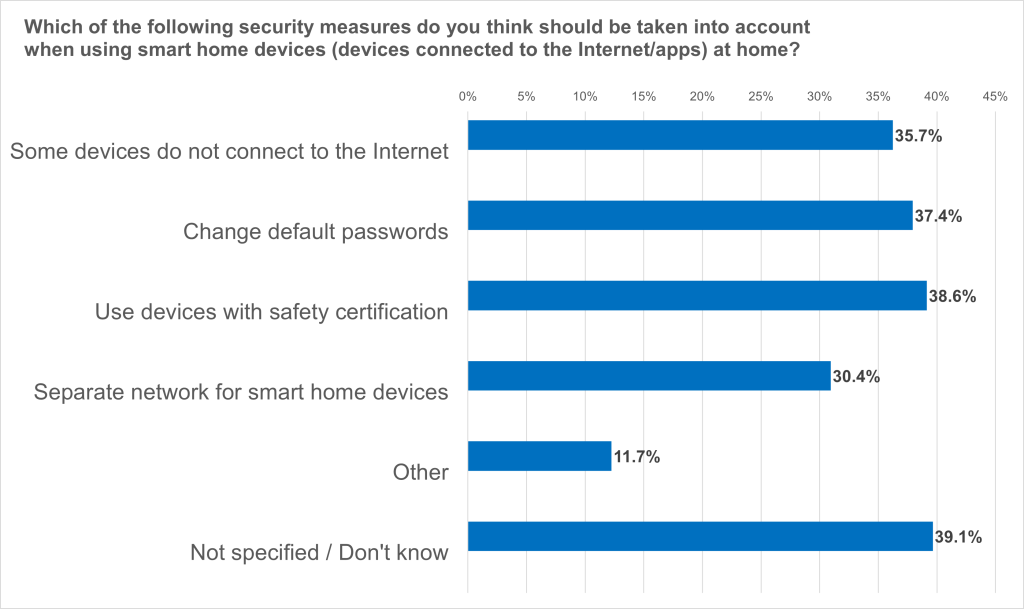
- 60.9 per cent mention security measures to be observed when using smart home devices
- Certificates, updates and separate networks for smart home devices increase security against cyber attacks
- New episode of the eco German-language podcast “Das Ohr am Netz (the ear to the Internet)” on the topic of smart homes
From intelligent lighting and heat monitoring to connected household appliances and smart consumer electronics: almost every second German (38 per cent) uses smart home devices. Smart entertainment electronics such as smart TVs are the most popular (26.1 per cent). Smart speakers such as Alexa or Google Home are also found in many households (13.7 per cent), as are smart heating or lighting controls (11.6 per cent). Smart household appliances such as smart refrigerators are only found in 4.5 per cent. These are the results of a representative Civey survey commissioned by eco – Association of the Internet Industry.
“Smart home technologies have the potential to enrich people’s lives and give them more control over their living spaces,” says Markus Schaffrin, Head of Member Services at eco – Association of the Internet Industry. “However, connecting these devices also brings new challenges, especially in terms of security.”
Security awareness among the population
Most people in Germany (61.4 per cent) are aware of possible security risks and name security measures to be observed in a Civey survey. 38.6 per cent only want to use devices with security certification, 37.6 per cent say they should change default passwords, and 35.7 per cent do not want to connect some devices to the Internet. “Consumers play an important role in the security of their smart home devices. By being aware and implementing some best security practices, they can minimise the risk of cyber attacks,” states Schaffrin. But which measures really make sense to protect your own connected home and network from attacks?
- If possible, do not connect older-generation devices to the Internet.
Older devices are usually not provided with updates and do not yet carry a security certificate. Special care should be taken with devices that process sensitive data, such as smart door locks and surveillance cameras. If possible, such devices should only be connected to their base station (gateway), which takes over control tasks, and not directly to the Internet. - Change default passwords
The standard passwords of many smart home devices can be easily searched on the Internet and are the most frequently used gateway for cybercriminals. Therefore, default passwords should be changed immediately. A risk remains if units have maintenance access whose password is set by the manufacturer. - Pay attention to security certificates
Consumers minimise their risks if they look out for security certificates such as the “IT security label” of the German Federal Office for Information Security (BSI). It enables “real-time monitoring”. Through a QR code on the device, users can check daily whether there are any vulnerabilities or available security updates. - Separate networks for smart home devices and sensitive data
If you operate an extensive smart home with many devices, it is worthwhile to operate a separate network for these devices. This minimises the risk of attackers using insecure smart home devices to access sensitive data on the user’s computer, tablet or mobile phone. It is also possible to control the flow of data in this network in order to get back keys to sunauthorised accesses. If the smart home devices are supposedly off, but there is still a lot of traffic on this network, the coffee machine, for example, could also be working for someone else who is using it for cyber attacks such as DDoS attacks. - Software must be kept up-to-date
Users should regularly inform themselves about updates and install them. For this purpose, it can be helpful to create your own list, enter all devices in it, and check them at certain intervals. - Use all available security mechanisms
If devices also offer the possibility of further security mechanisms, such as 2-factor authentication, then users should also use these.
Download graphic
Download graphic